intro
Properly managing users is crucial for any DBA – in this blog, we‘ll tell you how to propely manage users in a MySQL relational database system. Have a read!
Users are an absolutely necessary part of any database management system, and MySQL is no exception. Properly managing users within your MySQL database can be a matter of life and death – and while the main user provided by MySQL (the “root” user) has all privileges and is essentially the “God” in all aspects, there are multiple other things you should know to properly work with and manage your databases. Let’s roll!
Database User Management Explained
Before jumping into users in MySQL, we want you to be aware of the basics – users in databases should be treated just like any other user in any other piece of software. Databases are not an exception – in MySQL and other database management systems alike, users are used to run queries: before running a query, MySQL checks whether a certain user has the permission to run it, then proceeds accordingly: runs it and returns results or responds with an error. A query like so will provide us with a list of all users existing within MySQL – WHERE clauses can be used as well:

MySQL Users Explained
As you can probably tell, MySQL comes with three default users – these are the mysql.session, mysql.sys, and root users. These three users within MySQL are reserved for special use cases:
Besides those users, MySQL will also list all other users that were created by the user itself (see example above.) It’s nothing revolutionary, really – DBAs grant users privileges, and those privileges are then used to work with data. The more privileges are assigned, the greater the power of the user.
MySQL 8 also has these things called roles – roles are essentially collections of privileges that are assigned to a specific user. The more privileges a role has, the more powerful the user.
Working with Users and Privileges in MySQL
For now, we have provided you the basics – users have privileges, these privileges can often turn into roles. However, that’s far from the end – run a query like DESC user and you will indeed see that the privileges provided by MySQL are rather numerous:
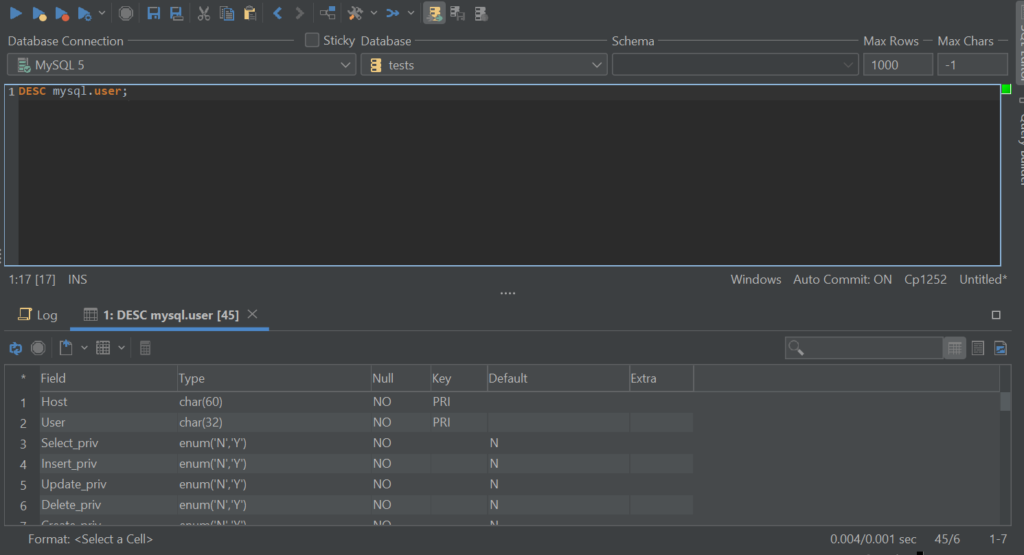
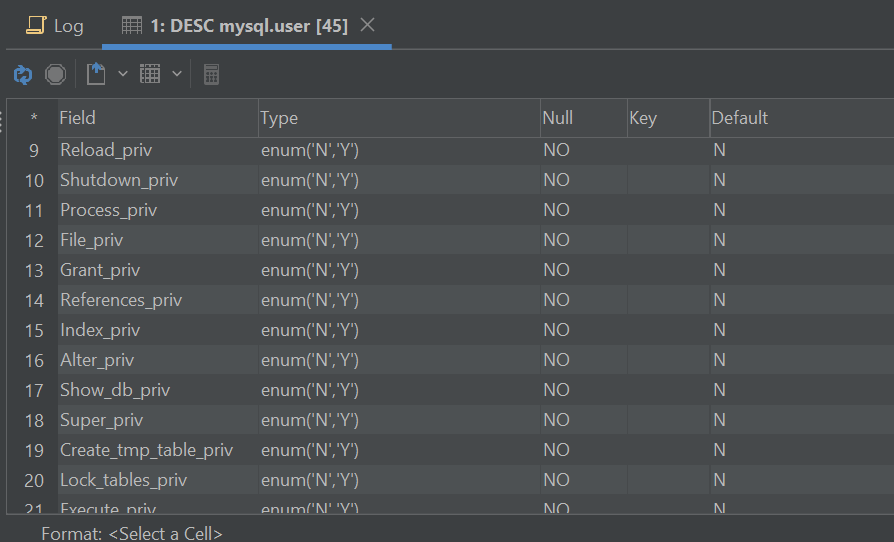
That’s because MySQL has thought of everything – from the users being able to show databases to work with files inside set directories and locking tables: there are privileges for everything. And that’s not without a reason, either – developers often are advised against working with their databases by using the superuser provided by MySQL. That’s because if the password of that user gets compromised, we can say goodbye to our databases and everything within – to add to that, the root user has many privileges that are simply not necessary to complete tasks related to daily DBA work, so instead, DBAs and devs turn to privileges. Here’s what you need to know about those on a high level:
| Security Level | Set These Privileges |
|---|---|
| High | CRUD (INSERT, SELECT, UPDATE, DELETE) |
| Medium | CRUD and Alter, Index, Reload, and Shutdown privileges |
| Low | CRUD, Alter, Index, Reload, and Shutdown privileges, the FILE privilege (allows to insert data into MySQL from a file), the GRANT privilege if there’s a necessity to grant roles to users, etc. |
The bottom line is this – the less privileges are assigned, the more secure your database will be. The same goes for roles (privilege collections) – to work with them, create a role (#1), grant it privileges (#2), then assign that role to a specific user (#3) – make sure to not go overboard when assigning privileges and you should be good to go:

Roles are only available in MySQL 8 and above, so even if you decide to not use them, there are a couple of other things you can do as well – one of them is always keeping in mind that the primary user within MySQL will still reside inside of your databases, and to further the security of your database, it can be renamed by running a query like so:

Of course, think of a better name than „notroot“, but you get the idea. Now the root user will be obfuscated and less simple to enumerate by attackers – to further the security of your user, consider putting its password inside of my.cnf like so – such an approach will let you log in to MySQL via the CLI without providing the password for the user (the password, if provided via the CLI in a traditional fashion, can be observed by observing the command history):
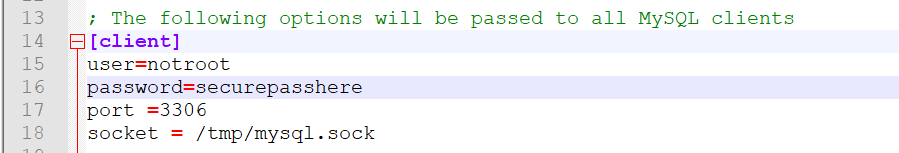
Once that’s done, feel free to log in to mysql using this approach (note that there’s no password):
$
mysql -unotroot [database_name]
Those who want to dive even deeper should consider creating accounts that can only access some part of their servers (see example below) and use them for management instead while keeping the root account obfuscated – a query like the one below will create a new_user and let it connect from any host in the example.org domain:
Protect your users with a secure password and these tricks will take your database further than you could imagine!
Partial Revokes & Other Tricks


After your users are secured with a strong password and you keep the tips given above in mind, always abide by security best practices, avoid re-using passwords in more than one place, and you should be good to go!
We hope that this blog has taught you something new in the database space, make sure to explore the blog of DbVisualizer to learn more about databases and their functionality in the future, and until next time!
FAQs
What Is User Management in MySQL?
In MySQL, user management refers to the tools and processes used to manage users who work with data in the databases and tables within MySQL and its flavors.
How Do I Secure Users in MySQL?
Use strong passwords, consider using the security plugins provided by MySQL, and make sure to use proper privileges. For maximum security, consider using SQL clients like DbVisualizer as they come with multiple features relevant to database security, as well as data breach search engines like BreachDirectory to check if you or anybody within your team is at risk of identity theft now or in the foreseeable future.
Where Can I Learn More About MySQL Security?
You can learn more about the security measures MySQL takes to secure its users over at its documentation or on our blog called TheTable.