intro
In this blog, we walk you through the security measures that can be used to secure any database management system. Have a read!
These days, security is paramount. Almost every day we hear about data breaches that have impacted the infrastructure of some company – more often than not, data derived from a data breach at a certain service also gets leaked and is archived in data breach search engines letting people measure the impact of their exposure. In this blog, we‘ll walk you through a couple of basic security measures you can apply to better secure the most precious asset of your company – data within your databases.
The Basics of Database Security
For many, database security encompasses one or more of the following categories:
Each of the outlined categories is vital for the security of our data – access control lets us batten down access privileges to strengthen the security of the data within our database instances, ensuring our users have only the proper privileges to access certain sets of data helps us ensure that we follow the „need to know“ principle (people should only know things that help them do their work and not anything else), plugins might help us plug certain security issues applicable to specific use cases (e.g. enterprise plugins will provide us with a firewall to further secure our data, etc.), and following general security advice will help us stay on track of the latest security developments applicable to our database management system of choice. We will first walk you through the overview of the applicable concepts, then demonstrate them in practice.
Access Control & User Security
The first thing many people think about when they think about security within databases is access control and user security. In most cases, these two things are very closely intertwined – users have privileges that ensure access control. Access control, on the other hand, ensures the security of the users within a database.
Good access control means that a user should not be able to access things that he or she does not necessarily need to know about – user security, on the other hand, pertains to using strong passwords that are preferably generated by a password manager.
Plugins
Plugins are another important part of database security – in many cases, plugins are also split into a couple of categories (authentication, connection control, password validation, etc.) and each of them provides users with the ability to further batten down a specific part of their database. Plugins are offered by pretty much every database management system that exists and for the most part, they‘re free, however, there also are enterprise-level security solutions that offer users the ability to use firewalls, for example. Enterprise-level security solutions are far from free and they can cost thousands of dollars, but for those who are paranoid about the security of their database instances and need to adequately batten down and secure everything that exists, they‘re certainly a viable option.
General Security Advice & Documentation
As far as general security advice goes, it‘s all pretty basic: all developers who have previously worked with web applications will know a couple of security measures applicable to databases as well. They will know how best to protect their applications from SQL injection, know a thing or two about filtering data.
People turn to the documentation when they‘re facing problems regarding the implementation or inner workings of their database management system and for the most part, they read only the security advice that‘s applicable to their specific use case. When they don‘t find much information there, they turn to StackOverflow and other sources and obtain information to tackle their security issues from there – StackOverflow has this DBA section where database experts help their less experienced counterparts to solve performance, availability, and, of course, security problems applicable to databases.
For the most part, documentation surrounding security issues in database management systems is clear and concise allowing us to find just what we‘re searching for – MySQL, for example, covers the following:

If you are looking for an easy and powerful SQL client and database manager, then you've got to try DbVisualizer. It connects to nearly any database.
MySQL links to these resources at the beginning of their security chapter – so do other database management systems. By doing so, they let people who‘ve already identified the problem they‘re facing head straight into how to solve it. Easy!
Applying Best Practices to Secure Your Database
Knowing security measures that we can apply is awesome, but applying them is another issue altogether. Here‘s how best to apply the security advice provided to you.
First, start from the basics – review your code and make sure it‘s not susceptible to SQL injection, install a web application firewall if necessary (these kinds of appliances can protect your web application from all kinds of attacks including the infamous SQL injection attack, DDoS attacks, Cross-site Scripting attacks, etc.), consider implementing brute-force protection into your login form to prevent credential stuffing attacks (credential stuffing is a practice when data taken from a data breach from one service is used to perform a data breach into another service), then move on to access control and user security as the first steps to ensure security in databases from the inside.
As far as access control and user security are concerned, first make sure that all of the users having privileges to access any part of your databases have strong passwords in place – that can be done by resetting the password of a specific user to a stronger one, then flushing the privileges (refreshing them so the database takes note of the changes.) For MySQL, the process looks like the following – a single query will do, just don‘t forget to issue a FLUSH PRIVILEGES query afterward:
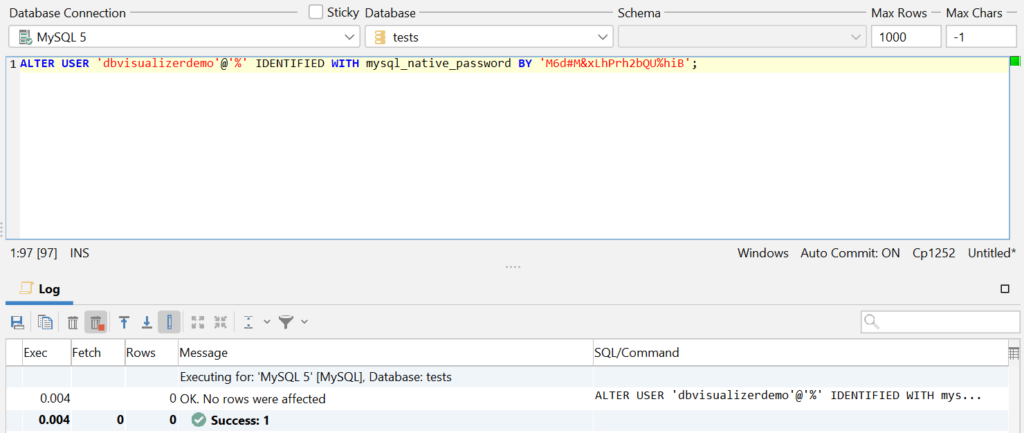
To ensure proper access control, first evaluate your options – head over to the docs of your database management system of choice and familiarize yourself with the available options, then choose a set of privileges applicable to a specific user (in this case, follow the „need to know“ principle: only choose privileges that are absolutely necessary), then grant them to the user using the GRANT query:

In this case, also keep in mind that most database management systems (the aforementioned example is based on MySQL) let you choose what kind of privileges should be applicable to what database. In the example above, we‘ve granted the SELECT and INSERT privileges to a user on the tests database (we can also grant privileges to a specific table by replacing the wildcard above with the table name.)
After this, you might also want to glance into the security plugins offered by your database management system. For MySQL, these plugins are MySQL Enterprise Firewall and MySQL Enterprise Audit – the firewall guards the database against the most prominent security threats and provides security in real-time, automatically creates an allowlist of approved SQL statements, and automatically blocks hacking attempts. The auditing plugin, on the other hand, allows users to seamlessly add an auditing solution into their database and implement stronger security controls to satisfy compliance with regulations like GDPR, HIPAA, and the like.
Enterprise solutions come with a downside, though – in many cases, they‘re incredibly costly to operate and maintain due to their nature, so many people turn to universal database management tools as a result.
Database Management Tools and Database Security
Many of these database management tools do not only provide a safe haven to manage their data, but come with capabilities that help improve database security as well – for example, head over to the tool properties tab in DbVisualizer (click Tools, then Tool Properties), and you will see an area that allows you to set a master password to protect your database, SSH, and proxy passwords for increased security – if you want to, you can also instruct DbVisualizer to require a master password on new connection attempts as you can see below:

DbVisualizer also lets us to set permissions for the tool itself – one can set permissions regarding the SQL Commander (SQL editor), table data editor, the procedure editor, or permissions for connections into databases. Here‘s how it all looks like:

Suppose we set the SELECT queries to „Deny“ in the development phase – we‘ll see the following error message:

Many other database management software solutions don‘t offer such extensive security features – make sure to evaluate the capabilities of such tools before you elect to use them – check their blogs, security features, and ensure that they‘re a fit for your particular use case.
After checking out the capabilities of database management tools, don‘t forget to keep checking on the documentation of your database management system of choice to follow updates in the security space – follow updates, keep in sync with blogs, and think of security as a component of everything you build: do that, and your databases will certainly have a golden future.